The whole process to virtualize x86 code (for 32-bit or 64-bit) can be described in the following stages:
•Reading of sensitive blocks of code to protect: Code Virtualizer will search in the compiled application all the sensitive blocks that were inserted by the developer in his source code
•Create an unique Virtual Machine for the application: Code Virtualizer use its polymorphic engine to create a unique Virtual Machine to interpret the transformed virtual opcodes
•Convert original x86 opcodes into specific virtual opcodes: Code Virtualizer will convert the original x86 opcodes into specific opcodes that are only understood by the previously generated unique Virtual Machine
•Destroy the original x86 opcodes and redirect the execution to the Virtual Machine: Code Virtualizer destroys the original x86 opcodes and redirects the first instruction in the block to the Virtual Machine, executing the virtual opcodes instead of the original x86 opcodes
Code Virtualizer creates the unique Virtual Machine and the virtual opcodes in the last section of the PE file (or inside your own code in the Stealth Mode), leaving the PE files with the exact format as the original one and avoiding someone from recognizing that Code Virtualizer is present inside the application.
Code Virtualizer against Reverse Engineering
Code virtualization consists of the transformation of binary code from a specific machine into a different binary code that is understood by another machine. That is, the instruction set from a specific machine is converted into a new instruction set which is understood by a different machine. The following picture represents the transformation from a block of Intel x86 instructions into a new instruction set for another machine (specifically a RISC 32-bit CPU):

Code Virtualizer can generate multiple types of virtual machines with a different instruction set for each one. This means that a specific block of Intel x86 instructions can be converted into different instruction set for each machine, preventing an attacker from recognizing any generated virtual opcode after the transformation from x86 instructions. The following picture represents how a block of Intel x86 instructions is converted into different kinds of virtual opcodes, which could be emulated by different virtual machines.
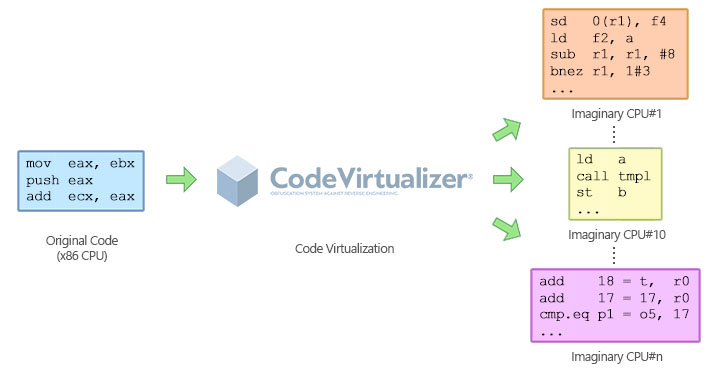
When an attacker tries to decompile a block of code that was protected by Code Virtualizer, he will not find the original x86 instructions. Instead, he will find a completely new instruction set which is not recognized by him or any other special decompiler. This will force the attacker to go through the extremely hard work of identifying how each opcode is executed and how the specific virtual machine works for each protected application. Code Virtualizer totally obfuscates the execution of the virtual opcodes and the study of each unique virtual machine in order to prevent someone from studying how the virtual opcodes are executed.
The following picture represents the image of an original compiled application (before being protected) and how it's transformed when it's protected by Code Virtualizer:
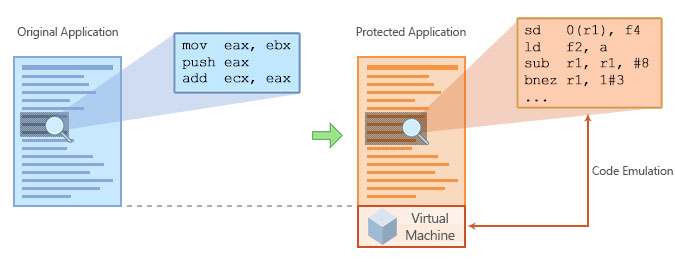
As the image shows, Code Virtualizer needs to embed the generated virtual machine at the end of the protected application (or inside your own code in the Stealth Mode) in order to emulate the virtual opcodes when they are going to be executed. The size of the virtual machine can vary from 500Kb to more than 3Mb! (depending on the Virtual Machine architecture selected). You can also Compress the generated Virtual Machine and virtualized code to decrease the size of your final application on disk.