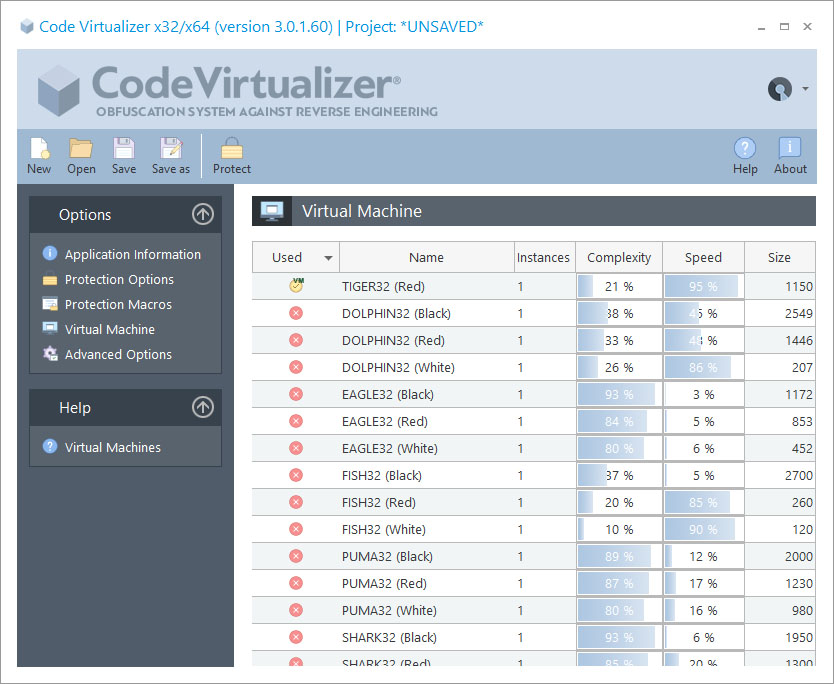
Available Virtual Machines
This panel shows all the available Virtual Machines that can be used in a protected application. Some Virtual Machines are public and others are private for specific customers. You can contact us at info@oreans.com to know more about customized Virtual Machines.
Suppose that you protect the same application two times using the TIGER Virtual Machine. Each protected instance will contain a unique TIGER Virtual Machine with different registers, instruction handlers, opcode table, etc. from the previous instance. They will just share the internal skeleton of the TIGER architecture. A cracker will have to study the internal skeleton of the TIGER architecture an later try to find a way to to attack all different variations of the TIGER architecture. This scheme is the one that contains all current software protectors based on Virtual Machines (they use mutations/variations of an internal architecture model defined by them).
We wanted to go one step further, creating multiple Virtual Machine architectures with the help of our powerful Virtual Machines Generator tool. Comparing two different architecture names, like TIGER and LION, is equivalent to comparing an Intel x86 processor with an ARM processor. Each one is totally independent from each other and developed without the other in mind.
The Complexity and Speed bars show some stats about the execution speed and the complexity of a given Virtual Machine. Notice that depending on the internal Virtual Machine revision, those values might change (increasing or decreasing across versions).
The CPUs field allows you to specify the number of copies that will be generated for a given Virtual Machine architecture. Even using the same architecture name, the generated Virtual Machine will contain different registers positions, different handlers, different opcode table, etc. When you insert several CPUs for a given Virtual Machine, some protection code and your VM macros will be virtualized with any generated CPU.
Virtualization
If you are using (old) VIRTUALIZER macros (instead of specifying a name of a Virtual Machine in your macro) you can select which of your selected Virtual Machines will be used to protect those VIRTUALIZER macros that are not assigned to any specific Virtual Machine.
Guidelines to select Virtual Machines
Developers might feel confused about which Virtual Machine they should select in order to get the desired security for their applications. Some developers might have the idea of adding as many Virtual Machines and CPUs as possible to highly increase the security of their applications. This might not produce the effect that they want.
1.Just insert a single Virtual Machine or a couple of them. If you insert several Virtual Machines and CPUs, it will produce a big protected application on disk and memory, as some Virtual Machines can be bigger than 1Mb. Notice that if you select several Virtual Machines and they are not selected in the lower "Virtualization" panel, SecureEngine will not insert those Virtual Machines inside your application, as they will be unused by the protection (optimizing the final size of the protected application)
2.When using VIRTUALIZER macros in your application, you should avoid using the plain VIRTUALIZER macro and specify the Virtual Machine architecture that will protect a specific macro (example: "VIRTUALIZER_TIGER_RED_START/END"). This will allow you to use complex Virtual Machines for your most sensitive code and a lighter Virtual Machine for code that needs to be virtualized and executed with good speed.
3.From time to time consider updating your VIRTUALIZER macros to point to a different or newer Virtual Machine architecture. If you have been using the TIGER architecture for some time, you might want to select a different architecture in new versions of your application, to fight against crackers that have been behind your application for some time.